Sage Ai for CFOs: From reporting to real-time intelligence
Today’s SaaS CFO is expected to be far more than a financial gatekeeper. They are strategic partners to the CEO, trusted voices for investors, and...
Switchboard: 0344 880 61411 | Helpdesk: 0344 880 6155
3 min read
CPiO Limited : Mar 25, 2024 4:44:14 PM
.png)
The way we work has undergone a dramatic shift. Cloud applications, remote workforces, and the ever-growing threat landscape demand a new approach to network security. Enter Secure Access Service Edge, or SASE, a revolutionary concept that's transforming cybersecurity. This guide unravels the complexities of SASE backbone technology, making it easier for beginners to understand its core functionalities and benefits.
.png?width=504&height=360&name=SASE%20security%20(1).png)
Imagine your company's network as a castle. Traditionally, security focused on fortifying the castle walls (perimeter security). This involved firewalls and intrusion detection systems (IDS) at the main entry point. However, the rise of cloud applications and remote work created new vulnerabilities. It's like having backdoors to the castle that bypass the main gate.
SASE offers a more holistic approach. It's like building watchtowers (security services) throughout the kingdom (network) and equipping your guards (users) with advanced communication tools. This ensures consistent security regardless of location or access point.
The SASE backbone is the hidden hero behind this security transformation. It's a globally distributed network of interconnected points of presence (PoPs) that act as the foundation for SASE services. Here's a breakdown of its key features:
The SASE backbone serves as the platform for a variety of security services delivered as a cloud service (SaaS). These services work together to provide comprehensive protection:
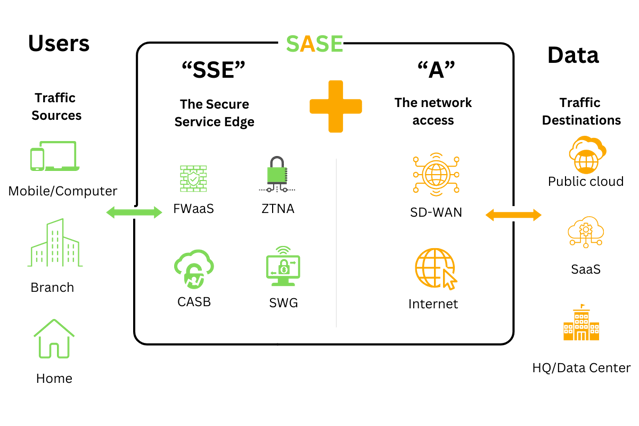
By leveraging the SASE backbone, these services can be delivered consistently and efficiently to all users, regardless of their location or device.
A robust SASE backbone offers a multitude of advantages for businesses:
As SASE gains traction, numerous vendors are entering the market. Here are some key factors to consider when selecting a SASE provider:
CPiO has an expert cyber security team, is Cyber Essentials achieved and can give you specific and preventive advice.
Don't leave it until you have suffered a cyber attack. Talk to one of CPiO's technical security experts who can advise you on policy and solutions.

Today’s SaaS CFO is expected to be far more than a financial gatekeeper. They are strategic partners to the CEO, trusted voices for investors, and...

Independent research firm Information Services Group (ISG) has classified Sage X3 as a Leader in its evaluation of ERP solutions for midsized...

Independent analyst ISG has positioned Sage X3 as a Product Experience Leader for mid-sized manufacturing organisations.
Keep up to date with CPiO's latest blogs, news and events
.png)
In part one of this blog series, we discussed some of the platform policies that you can put in place to minimise your risks. It is now time to...

With a high level of fraudulent emails and illicit messages circulating at present, some under the guise of NHS and Government Covid-19...

For small and medium-sized enterprises (SMEs), choosing the right ERP system can be challenging. With multiple deployment options available, it’s...